Even worse, it's a "Day Zero" exploit - no security patch is available for you to protect yourself. Exploit code is circulating, so there's a chance that the Bad Guys might have a "party at your place", and you know what a mess they'll leave behind. Fortunately, it's super easy to protect yourself:
Step 1: Start Adobe Acrobat Reader. For Windows users, you'll go to your Start menu, and Acrobat 9 is probably there.
Step 2: Go to the Edit menu, and select Preferences.
 Step 3: Highlight "Javascript". The box labeled "Enable Acrobat Javascript" is probably checked. Click the box to get rid of the check.
Step 3: Highlight "Javascript". The box labeled "Enable Acrobat Javascript" is probably checked. Click the box to get rid of the check.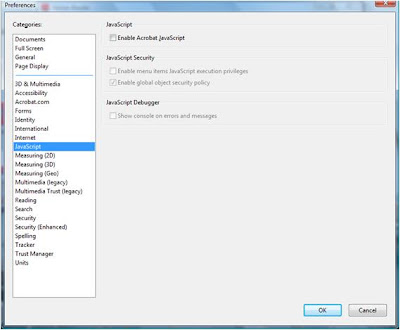 Step 4: Click "OK". Bravo - you're safe. No pwn you long time for you (at least via PDFs, at least by this method).
Step 4: Click "OK". Bravo - you're safe. No pwn you long time for you (at least via PDFs, at least by this method).Don't worry about losing Javascript - this only effects Acrobat reader, not your browser. Not that it's not more security to control Javascript in the browser (Firefox users can take a look at noscript), but it breaks lots of Al Gore's Intarwebz.
UPDATE 16 May 10:43: Patch is available now.
8 comments:
Thanks, just did it.
No extra charge, Hammer. All part of the service.
;-)
Thanks man!
I don't know squat, but I have done every security measure you have recommended.
Regards,
Albert
The Rasch Outdoor Chronicles.
The Range Reviews: Tactical.
Proud Member of Outdoor Bloggers Summit.
You're welcome, Albert. A lot of security is pretty easy if you have a roadmap.
Thanks Ted!
Wow, that sucks. Acrobat's JS is the main way you make it do stuff. Oh well. Sucks for Adobe.
Chris, I think that the Day Zero exploit circulating right now is Exhibit A in the case of "Why it's A Bad Thing to let PDF 'do stuff'."
;-)
And I seem to be getting some interesting attention from folks at Adobe, according to Sitemeter.
I bet you are. They try to sell PDF as a good way to have forms be filled out and such. I have always thought it was stupid, but what do I know.
Personally using a postscript file for data entry has always seemed a bit unatural, and possibly against everything that is sacred.
Post a Comment